Aagya Khatri on Feb 05, 2026
Reading Time: 7 Min
Cloud businesses are evolving faster than ever, and so are the risks, including occasional data exposure incidents, DDoS attacks, and other cybersecurity threats.
As SaaS spending on development climbs, you should ask yourself, how secure is your app and data? Without security, your thousand-dollar SaaS app will crumble.
The solution is assessing SaaS security, a cutting-edge technology-driven approach that monitors, protects, governs, and controls SaaS environments in real-time and offsets threats, while maintaining uninterrupted business growth. AI-based threat detection, user behavior monitoring, and security posture management are a few examples you should consider.
Let us take you through a brief guide to adopting modern security measures to ensure SaaS security, suitable for enterprises and startups alike.
What You Should Know About SaaS Security?
SaaS growth improves speed and flexibility and drives innovation in businesses. But it also means more apps, users, and data are being spread across multiple cloud platforms, highlighting that technology environments have become increasingly complex and precarious.

Ransomware, supply chain attacks, and downtime account for the majority of cyberattacks, causing business losses, legal and regulatory fines, and operational disruptions.
SaaS is not immune to these security risks. Unlike traditional IT security, SaaS security focuses on protecting applications hosted by third-party providers such as Google Workspace, Microsoft 365, Salesforce, Slack, Zoom, and Notion that store confidential information. A threat to SaaS may compromise the security of third-party apps, risking everything.
Likewise, users can log in from anywhere on any device, which means data is shared across multiple providers, making tracking, monitoring, and managing security more difficult than in traditional systems.
Therefore, a single breach can expose millions of customer records, resulting in significant financial losses and even lawsuits.
Here is where most enterprises fail in securing their apps.
- Lack of identity and access management to control who can log in and what they can do.
- Lack of stealth data protection measures to prevent leaks, theft, or unauthorized sharing.
- Lack of early and real-time threat detection to identify suspicious behavior and cyberattacks.
- Failure in compliance monitoring to meet regulatory requirements.
- Failure in SaaS posture management to reduce misconfigurations and risky settings.
Furthermore, modern cybercriminals increasingly target SaaS platforms because they are lax on security measures.
- Remote and hybrid work expands SaaS exposure.
- Employees use multiple SaaS apps daily, increasing risk.
- AI-powered cyber threats have become more advanced.
- Compliance requirements have become increasingly stringent globally.
- SaaS environments grow faster than security teams can manage.
How to Strengthen SaaS Security
Instead of relying solely on firewalls or on-site security, enterprises should secure cloud-based software by monitoring user logins, data flows, and app configurations in real time to control access, detect threats early, and prevent data leaks.
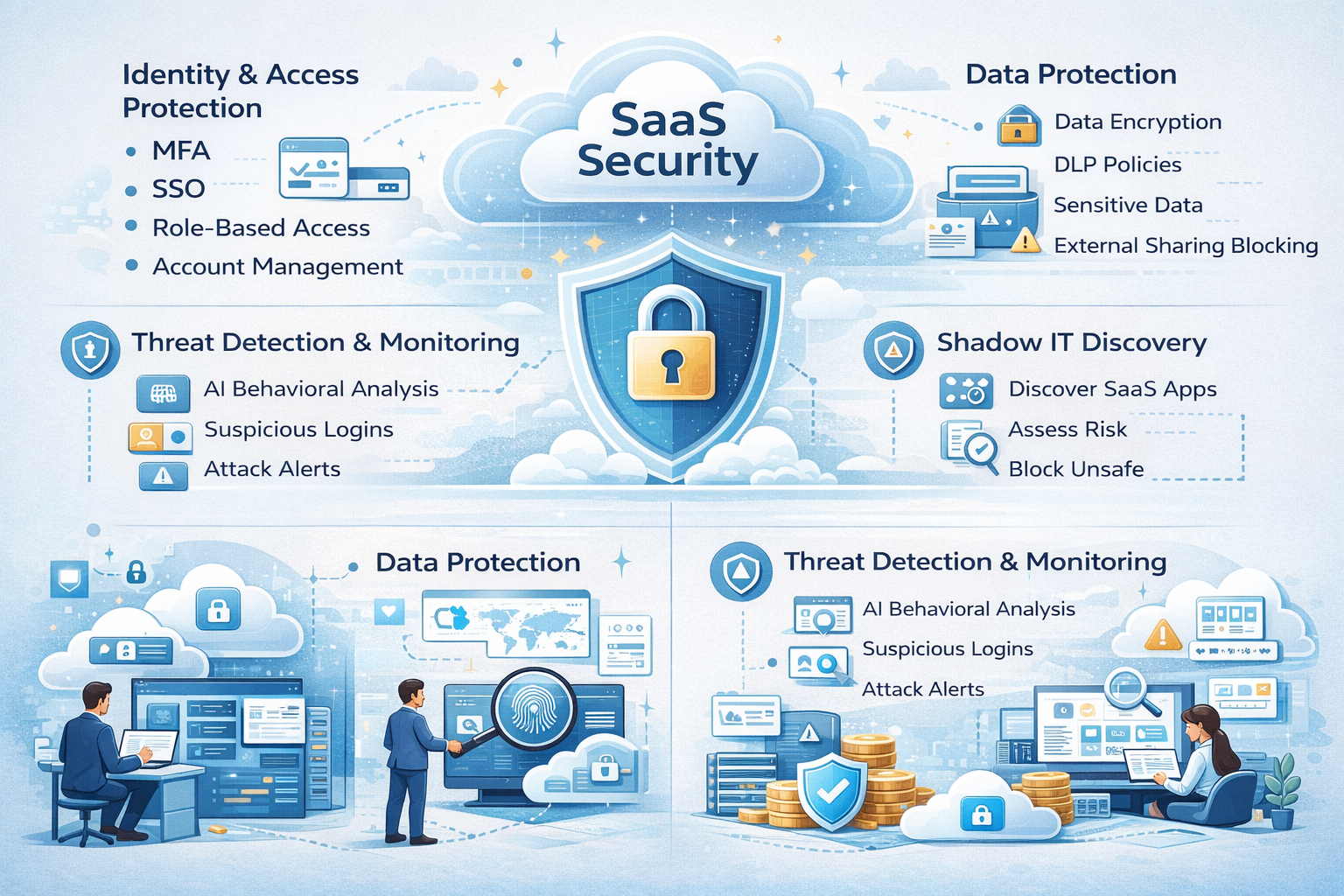
SaaS security is built on several key pillars that work together to protect cloud-based applications. Each pillar addresses a specific risk area.
1. Identity and Access Protection
Did you know 99% of cloud security failures are the user's fault, such as leaving SaaS databases publicly accessible?
Access management ensures that only legitimate users can access SaaS applications and only to the extent necessary for their jobs, preventing unauthorized logins, stolen credentials, and other security risks.
By managing authentication, permissions, and account lifecycle events, organizations reduce exposure to insider threats, phishing attacks, and privilege abuse.
- Multi-factor authentication (MFA).
- Single sign-on (SSO).
- Role-based and least-privilege access.
- Account lifecycle management.
2. Data Protection and Loss Prevention
This pillar focuses on protecting sensitive information from leaks, theft, or accidental exposure, ensuring that the confidential data, such as customer records, financial files, and intellectual property, remains protected whether stored, shared, or accessed remotely.
Ensuring data security compliance, including GDPR, HIPAA, and PCI-DSS, helps detect risky actions. Remember to consult with system engineers regarding:
- Data encryption.
- Data Loss Prevention (DLP) policies.
- Sensitive data classification.
- Blocking risky external sharing.
3. Threat Detection and User Behavior Monitoring
In addition to defending against external hackers, this pillar monitors activity within SaaS platforms.
AI-based security measures analyze user activity patterns to detect suspicious behavior, including unusual login locations, multiple login attempts, abnormal downloads, and attempts to access restricted resources, and apply appropriate security measures to deter the attacks.
Take a look at this.
|
Security Area |
AI/ML-Based Measure |
What It Protects Against |
Examples / Tools |
Typical Cost (USD / month) |
|
Threat Detection |
Behavioral anomaly detection |
Zero-day attacks, insider threats, unusual login or API behavior |
Darktrace, Vectra AI, AWS GuardDuty |
$300 – $3,000+ |
|
Authentication & Access |
Adaptive / risk-based authentication |
Credential stuffing, account takeovers |
Okta Adaptive MFA, Microsoft Entra ID AI |
$2 – $6 per user |
|
API Security |
ML-based API traffic analysis |
API abuse, data scraping, bot attacks |
Salt Security, Noname Security |
$500 – $5,000+ |
|
Fraud Prevention |
Transaction pattern modeling |
Payment fraud, fake accounts |
Stripe Radar, Feedzai |
$0.02–$0.10 per transaction |
|
Malware Protection |
AI-based malware classification |
Advanced malware, ransomware |
CrowdStrike Falcon, SentinelOne |
$8 – $20 per endpoint |
|
Data Loss Prevention (DLP) |
ML content classification |
Data leaks, sensitive data exposure |
Microsoft Purview, Nightfall AI |
$4 – $10 per user |
|
Bot Management |
AI bot behavior analysis |
Credential abuse, scraping, fake traffic |
Cloudflare Bot Management, Akamai |
$200 – $2,000+ |
|
Cloud Misconfiguration |
ML risk scoring & drift detection |
Misconfigured storage, IAM errors |
Wiz, Palo Alto Prisma Cloud |
$400 – $4,000+ |
|
Endpoint Security |
Predictive endpoint monitoring |
Device compromise, lateral movement |
CrowdStrike, Carbon Black |
$8 – $18 per device |
|
Log & SIEM Analysis |
AI-driven log correlation |
Missed alerts, alert fatigue |
Splunk AI, Elastic ML SIEM |
$500 – $10,000+ |
|
Phishing Detection |
NLP-based email analysis |
Phishing & social engineering |
Darktrace Email, Abnormal Security |
$3 – $7 per user |
|
Compliance Monitoring |
AI compliance posture tracking |
SOC2, HIPAA, GDPR drift |
Secureworks Taegis, Drata AI |
$200 – $2,000+ |
By identifying potential threats early, organizations can respond quickly to compromised accounts, insider risks, or automated attacks before damage occurs.
4. SaaS Security Posture Management (SSPM)
Many breaches occur due to weak default settings, overly permissive access rules, or misconfigured sharing controls.
SSPM ensures SaaS applications are configured securely and follow industry best practices. It continuously scans SaaS environments to:
- Identify risky settings.
- Fix misconfigurations.
- Enforce compliance standards.
- Reduce attack surfaces.
Key measures include hardening app-specific settings, detecting configuration drift from secure baselines, managing OAuth integrations, and enforcing least-privilege access to ensure compliance with regulations such as GDPR and HIPAA.
5. Shadow IT and SaaS Discovery
Employees often use unauthorized or unknown SaaS tools outside official IT oversight, creating hidden security risks.
Did you know unsanctioned use of AI tools added $670,000 in costs to breaches in 2025?
This pillar helps organizations discover these tools, assess their security impact, and decide whether to approve, restrict, or block them.
- Discovering hidden apps.
- Evaluating security risks.
- Blocking unsafe platforms.
- Improving SaaS governance.
Key solutions include Cloud Access Security Brokers (CASBs), SaaS Management Platforms (SMPs) such as Josys and Zylo, network monitoring tools that scan for unauthorized applications, user training, and faster procurement processes.
By improving visibility into SaaS usage, companies gain better control over data flow, reduce unapproved access points, and strengthen governance across cloud applications.
Conclusion
SaaS security helps organizations protect their cloud tools without slowing work or innovation.
It keeps user accounts safe, protects sensitive data, monitors risky behavior, and controls SaaS usage. When done well, SaaS security builds customer trust, supports employees, and enables secure growth in a cloud-first world.
Contact Searchable Design, the best SaaS development agency to outsource your SaaS development, security, and management projects.
Comments(0)
Your email address will not be published. Required fields are marked *
Recommended Posts
Unlock the Secret of Power BI to Empower Your Data Analysis
Turn Raw Data into Real-Time Intelligence with Power BI
Why More Startups Are Offshoring Data Engineering Roles in 2025
Unlocking Global Talent for Faster, Smarter, Scalable Growth through Offshoring Data Engineering
How to Empower Your Web Development Project in 2025?
Empowering Your Web Build with the Right Strategy, Stack, and Global Talent Network
RECOMMENDED TOPICS
TAGS
- offshoring
- outsourcing
- web development
- digital marketing
- artificial intelligence
- offshore
- it support
- data analytics
- saas
- agile methodology
- pms
- project management system
- data
- data centric approach
- customer insight
- cybersecurity
- it infrastructure
- it sustainability
- cloud computing
- agentic ai
- business process automation
- voice search optimization
- seo
- tiktok
- growth hack
- app development
- data engineering
- global talent pool
- techical consulting
- power bi
- business intelligence
- backoffice
- communication
- outsource
- remote team
- it roles
- project management
- data engineer
- content development
- business development
- offshore talent
- legacy software
- insurtech
- insurance
- web security
- off
- data decision
- test
About
Data Not Found
NEWSLETTER
Related Posts
How AI is Empowering SaaS Adoption? Tips for Startups and Enterprises
Turning software from static tools into intelligent, self-guided experiences


